So I’ve returned to this topic and tried it on another computer in the network. It’s what I’ve designated the “admin-PC” for the network and verified that this one doesn’t have that FIPS non-sense going on it it.
With that out of the way - the problem now became that Certify was using SFTP for the SSH (remote) authentication method to upload the cert bundle (.pfx) which my target device doesn’t support. It only support SCP. So I figure out how to use PuTTY scp on the command line and figure I’ll just make a “Run…” task.
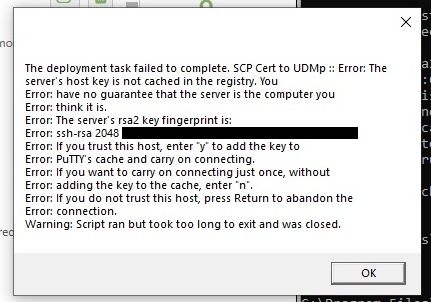
Now the first time through - PuTTY scp states, hey I don’t have the RSA key fingerprint on record so I can’t verify who I’m connecting to. But, at the command line, I type “Y” to accept that key and add it to PuTTY’s key cache. Subsequent executions now do not generate that error message.
So create my “Run…” task in Certify, I point Certify to the PuTTY scp .exe file, I copy the arguments and options over, and then save the task. Remember, I already saved the server RSA key to PuTTY’s key cache by first executing these command manually.
However, when I try to execute my “Run…” task in Certify using the commands created using the CLI - Certify hangs and then eventually fails saying it killed the task for taking too long and shows me that PuTTY was waiting for Certify to accept the RSA key of my server.
I don’t know what’s going on. This is the last step I need to get this update process fully automated so I don’t have to manually do anything anymore. I’m just getting frustrated. If it’s running PuTTY scp in isolation of the OS or in someway that means PuTTY can’t get to its keystone … then how do I script or automate pressing the “y” button to accept the RSA key.