I had the same (or similar) issue with wildcards - see https://github.com/webprofusion/certify/issues/384 - but to save the link this is what worked for me - using your domain as an example:
- Add the main domain to the cert domains you want - so freeparking.co.nz for you (could be any subdomain as well I think)
- Add the wildcard domain as the second domain to include - so *.freeparking.co.nz
Make sure the full domain in 1 above is marked as the primary
So it should look a bit like:
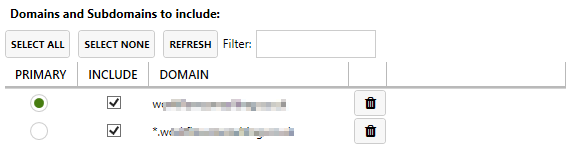
This then worked once TXT DNS dropped on to the top level domain- and I have renewed without having to change the DNS since too.