Hi,
in the current version of certify the chain is missing if your deploy to apache.
Output filepath for cert → works as expected
Output filepath for key → works as expected
Output filepath for full chain → leaf cert is inside but the chain is missing
Output filepath for CA chain → creates an empty file
I don’t no the versions excactly, but with 6.0.13 it works and with 6.0.18 it isn’t working .
Thx.
Hi,
Can you check your source PFX file has the intermediates in the chain (using certutil or openssl)?
Systems may vary depending on Key Type (RSA or EC) and whether the system already trusts the CA root properly.
I can confirm in my own testing just now on a production server using Deploy to Apache, issuing from Let’s Encrypt:
- cert.pem has leaf cert
- privkey.pem has private key
- fullchain.pem has leaf cert then intermediate cert (R11) in this case
- chain.pem has R11 intermediate
So there is something different happening in the chain building for your PFX. The app would previously fail to renew certs on systems that didn’t have the CA root in the Computer Certificate trust store ( Trusted Certification Authorities) and a common problem on windows is broken windows updates or CA root cert downloads disabled or blocked.
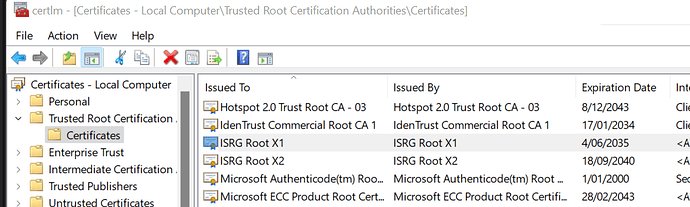
Can you check your system has ISRG Root X1 issued by ISRG Root X1 (not by DST Root CA X3)?
Yes, ISRG Root X1 is issued by ISRG Root X1
EC or RSA makes no difference.
Where can i find my source PFX file?
You can either export it using an Export Certificate task (as pfx) or you can find the current path under Certificate > Advanced > Actions , it will be under C:\ProgramData\certify\assets\
Now i can see the difference, this was before the issue persists:
================ Zertifikat 0 ================
=========== Verschachtelungsebene 1 anfangen ==========
Element 0:
Seriennummer: 912b084acf0c18a753f6d62e25a75f5a
Aussteller: CN=ISRG Root X1, O=Internet Security Research Group, C=US
Nicht vor: 04.09.2020 02:00
Nicht nach: 15.09.2025 18:00
Antragsteller: CN=R3, O=Let's Encrypt, C=US
Kein Stammzertifikat
Zertifikathash(sha1): a053375bfe84e8b748782c7cee15827a6af5a405
---------- Verschachtelungsebene 1 beenden ----------
Keine Informationen über den Schlüsselanbieter
Das Zertifikat und der private Schlüssel für die Entschlüsselung wurden nicht gefunden.
================ Zertifikat 1 ================
=========== Verschachtelungsebene 1 anfangen ==========
Element 1:
Seriennummer: 4001772137d4e942b8ee76aa3c640ab7
Aussteller: CN=DST Root CA X3, O=Digital Signature Trust Co.
Nicht vor: 20.01.2021 21:14
Nicht nach: 30.09.2024 20:14
Antragsteller: CN=ISRG Root X1, O=Internet Security Research Group, C=US
Kein Stammzertifikat
Zertifikathash(sha1): 933c6ddee95c9c41a40f9f50493d82be03ad87bf
---------- Verschachtelungsebene 1 beenden ----------
Keine Informationen über den Schlüsselanbieter
Das Zertifikat und der private Schlüssel für die Entschlüsselung wurden nicht gefunden.
================ Zertifikat 2 ================
=========== Verschachtelungsebene 1 anfangen ==========
Element 2:
Seriennummer: 04e81b0a92d0ed25ecc4bc1187e19965c388
Aussteller: CN=R3, O=Let's Encrypt, C=US
Nicht vor: 07.07.2023 12:54
Nicht nach: 05.10.2023 12:54
Antragsteller: CN=xxxxxxxxxxxxxxxxx
Kein Stammzertifikat
Zertifikathash(sha1): xxxxxxxxxx
---------- Verschachtelungsebene 1 beenden ----------
Anbieter = Microsoft Enhanced Cryptographic Provider v1.0
Verschlüsselungstest wurde durchgeführt
CertUtil: -dump-Befehl wurde erfolgreich ausgeführt.
This is the pfx now (issue still persists):
================ Zertifikat 0 ================
=========== Verschachtelungsebene 1 anfangen ==========
Element 0:
Seriennummer: 8a7d3e13d62f30ef2386bd29076b34f8
Aussteller: CN=ISRG Root X1, O=Internet Security Research Group, C=US
Nicht vor: 13.03.2024 02:00
Nicht nach: 13.03.2027 01:59
Antragsteller: CN=R11, O=Let's Encrypt, C=US
Kein Stammzertifikat
Zertifikathash(sha1): 696db3af0dffc17e65c6a20d925c5a7bd24dec7e
---------- Verschachtelungsebene 1 beenden ----------
Keine Informationen über den Schlüsselanbieter
Das Zertifikat und der private Schlüssel für die Entschlüsselung wurden nicht gefunden.
================ Zertifikat 1 ================
=========== Verschachtelungsebene 1 anfangen ==========
Element 1:
Seriennummer: 04bc35d00077042e962ee6377074390eaf81
Aussteller: CN=R11, O=Let's Encrypt, C=US
Nicht vor: 30.07.2024 14:42
Nicht nach: 28.10.2024 14:42
Antragsteller: CN=xxxxxxxxxxxxxxxxx
Kein Stammzertifikat
Zertifikathash(sha1):xxxxxxxxxxxxxxx
---------- Verschachtelungsebene 1 beenden ----------
Anbieter = Microsoft Enhanced Cryptographic Provider v1.0
Verschlüsselungstest wurde durchgeführt
CertUtil: -dump-Befehl wurde erfolgreich ausgeführt.
Between this two there was no certify version change, but i changed which fqdn is the primary for the cert.
Your previous chain was Leaf > R3 > ISRG Root X1 > DST Root CA X3
The current chain is leaf > R11 (or R10) > ISRG Root X1 (because Let’s Encrypt have updated their chain).
Something may be getting lost in translation but I can’t see a problem with the PFX.
Sorry, I can’t find a reason for this export problem and I’m unable to reproduce it on any of the machines I have. Which version of Windows are you running the app on and was it a fresh install of windows or an upgrade from an older version?
Just ran into this same issue using Google Cloud Public CA with a task to deploy to XAMPP/Apache.
Version 6.1.11.0
I can see the PFX contains the intermediate and root. but the chain.pem is empty and fullchain.pem only contains the cert.
domain cert = issused by WR1
WR1 = issued by GTS Root 1
GTS Root R1 = issued by GlobalSign Root CA
I’ll have to create a script that exports these until it is fixed or use another ACME client.
@bgoewert_seiler thanks, can you try the same with the latest v7 beta? I can confirm in my own tests with GTS that fullchain.pem includes the leaf and intermediate (WR1), and chain.pem contains just the WR1 intermediate.
-----BEGIN CERTIFICATE-----
MIIEbDCCA1SgAwIBAgIRAOdIzOqQ3+8cDXBjtMBJLqMwDQYJKoZIhvcNAQELBQAw
OzELMAkGA1UEBhMCVVMxHjAcBgNVBAoTFUdvb2dsZSBUcnVzdCBTZXJ2aWNlczEM
MAoGA1UEAxMDV1IxMB4XDTI1MTIwMzA3MDUwM1oXDTI2MDMwMzA3MDUwMlowIDEe
MBwGA1UEAxMVZ3RzLnByb2plY3RiaWRzLmNvLnVrMFkwEwYHKoZIzj0CAQYIKoZI
zj0DAQcDQgAEU1LjtUq96M7SwCbMAi+QDt5lbsqonDjGbsLGMrvJ9rpXrEe/poqZ
v9J49bU6c0A2J4XliI2TUZI17evyp1976KOCAk8wggJLMA4GA1UdDwEB/wQEAwIH
gDATBgNVHSUEDDAKBggrBgEFBQcDATAMBgNVHRMBAf8EAjAAMB0GA1UdDgQWBBTc
6J7bql7uExn8WhYgPfFfU/cv4DAfBgNVHSMEGDAWgBRmaUnU3iqckQPPiQ4kuA4w
A26ILjBeBggrBgEFBQcBAQRSMFAwJwYIKwYBBQUHMAGGG2h0dHA6Ly9vLnBraS5n
b29nL3Mvd3IxLzUwZzAlBggrBgEFBQcwAoYZaHR0cDovL2kucGtpLmdvb2cvd3Ix
LmNydDAgBgNVHREEGTAXghVndHMucHJvamVjdGJpZHMuY28udWswEwYDVR0gBAww
CjAIBgZngQwBAgEwNgYDVR0fBC8wLTAroCmgJ4YlaHR0cDovL2MucGtpLmdvb2cv
d3IxL3B0MGRCdURfT2k0LmNybDCCAQUGCisGAQQB1nkCBAIEgfYEgfMA8QB2AJaX
ZL9VWJet90OHaDcIQnfp8DrV9qTzNm5GpD8PyqnGAAABmuM+UvwAAAQDAEcwRQIg
LCevhWTVmadNc8zPSbJV9A9GPvAQv7wJ5OsyoBfMjVUCIQDFhnzkx/YWo/U6Pmum
It4UfJlmz1NXP+oPvl3F8XsXNAB3ABaDLavwqSUPD/A6pUX/yL/II9CHS/YEKSf4
5x8zE/X6AAABmuM+UvEAAAQDAEgwRgIhAK8w1Wjsf2qGz0Sydh3PSGXudjbZ7HcK
9o9Tc5hWKKFwAiEA3dZqC5OYSgRLm7aMd2YJ1gbOb06WNVOWuDHm699KzSUwDQYJ
KoZIhvcNAQELBQADggEBAAwfLBYoIhMZ4UnIOmuh/g48DoirVD8xQI50umbMMXDR
0yNfbMMppX9fYYZeOhxvOcvuQq4LjluLEeruSPp1FFrMU9UuVRKec3v0pOMuaChZ
WbuOdkrVla2aeQ80QR1u6PTV54Pm2qsMHj0bpoLQFgnWcyBTd60gSCfyga1lOlvL
lSLl0FtZ7IZ0lsPA3Q1YOIQKIsDW7VXJy+aQon9zIcIcSYl1DWyG3HOY1NGxCrDf
b4ptdZ0whC1CSNq51cqaCxke97QSexEIlnW9qkLB+WbWYoa50rlA8F0/BdmaNMqK
xjYiTaQT0Dz/q0CZoDJb+xAHXL4pkle/V8Mg9cHW7lQ=
-----END CERTIFICATE-----
-----BEGIN CERTIFICATE-----
MIIFCzCCAvOgAwIBAgIQf9niwtIEigR0tieibQhopzANBgkqhkiG9w0BAQsFADBH
MQswCQYDVQQGEwJVUzEiMCAGA1UEChMZR29vZ2xlIFRydXN0IFNlcnZpY2VzIExM
QzEUMBIGA1UEAxMLR1RTIFJvb3QgUjEwHhcNMjMxMjEzMDkwMDAwWhcNMjkwMjIw
MTQwMDAwWjA7MQswCQYDVQQGEwJVUzEeMBwGA1UEChMVR29vZ2xlIFRydXN0IFNl
cnZpY2VzMQwwCgYDVQQDEwNXUjEwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEK
AoIBAQDPbjYWircr7kaYAx1TcA937qNLoHK+jyMtwkfGj1yN+T3mGo7uMyINyRFI
uLBizvRpDXICfd7VJg/DbpvPfg7XIM/GkDujggbaOp3/bFa/3OlhlEXkabxPD8kT
wK1hRHIggdAPK55oamJqj4oiV3lpK+IkM352YyxdvFFpfiMHsf92gfHuuFi1azUV
76HmSCg5lzHZBx+Vp56uz5i8no2KA+Gwl01Qb5NMSh/4233xkJkVf+OW7e4xgepy
PVId3yVkpQtwqp7oqLlHyKdaECVgb0Lh1z/njwzwwoNGMyDmS3cEdqFop10VGO/Y
KHc1rQ6tRuRibuKq+MzvN34PJrMHAgMBAAGjgf4wgfswDgYDVR0PAQH/BAQDAgGG
MB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQcDAjASBgNVHRMBAf8ECDAGAQH/
AgEAMB0GA1UdDgQWBBRmaUnU3iqckQPPiQ4kuA4wA26ILjAfBgNVHSMEGDAWgBTk
rysmcRorSCeFL1JmLO/wiRNxPjA0BggrBgEFBQcBAQQoMCYwJAYIKwYBBQUHMAKG
GGh0dHA6Ly9pLnBraS5nb29nL3IxLmNydDArBgNVHR8EJDAiMCCgHqAchhpodHRw
Oi8vYy5wa2kuZ29vZy9yL3IxLmNybDATBgNVHSAEDDAKMAgGBmeBDAECATANBgkq
hkiG9w0BAQsFAAOCAgEATuazCBEgkWAn+VGQTQIY7rjBidUihJfm1t/mTjo7KQR+
3iDx4o2L06oeF0Q3wpKYpQgI/TeMqUlYMWQmZbWPE0PX8pfsVAE5E5tVOjh34bNA
JwDPVnsZVJwzN3nw5BGQ7sxRspFzIcM/qbbTpNeXf9II4Wsk2+Tv6FSVFZUL3/0u
HradbruDWjRQ4IZ7mYqKiEqk08dpOZ+TmBzwykEGy1/IXberb6Ap1SSnn2+RI7t6
N/fqPCrwwFjp8kg1G6etRATGBaPYCx+GjJMFPX+k97Alvoj3/98SvqdegLPYEPjv
xUclHpiKLD63NMmVarVQddIL6kOvTe5k0pnxRnR+mndGHIQc77TLbcZFeja56Pyn
lSqmer578c7CBrPqo1BVmPyWUK+v6sGuzs7Mq7QQaxVs4710cI/MpPp1ovxMVt17
ENKxLk34LpEKAKVmqwnzbHHRjhXNeCC984XDOwLEp0K4MzHl8ZOWJQAakCdVlFC+
PyA3GP2JX/QLoqWNHGuN9c9vLObDhHVs/L+65De+OdnnjpFGI9xxtsNyRsyaHdFA
f5z7ulOoXDXkHCCej/Ehs5docReNt16W2xbH/EBuirJrOzFE2rtALxksl1TdEjOf
IKXOJfUqQeVI5+hA7V+n1+A/n7Npg0S+5ODytWh5XW54ccN1drJnMK54ttozh0c=
-----END CERTIFICATE-----
A thing to try would be to remove the Deploy to Apache task, save the managed certificate configuration, then add Deploy to Apache again, this would fully clear any stray config. We did have an old issue where the underlying parameter config for a task could become duplicated and result in some empty files.
Further to this we have found an issue where if your windows host does not trust a root or cannot resolve the intermediates using the .net X509Chain.Build method then you could get unexpected results. We will fix this in the next 7.x update.