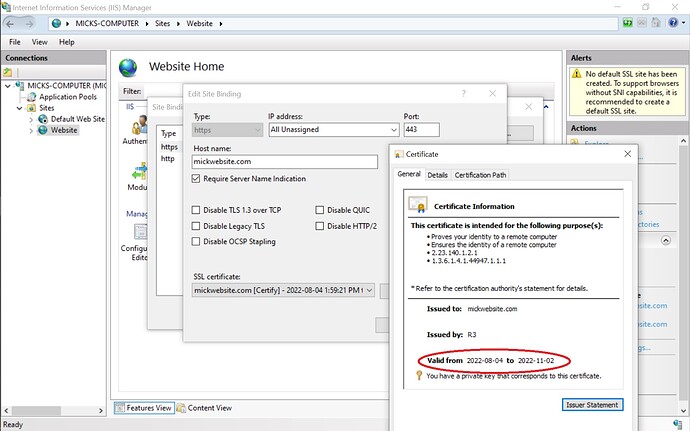
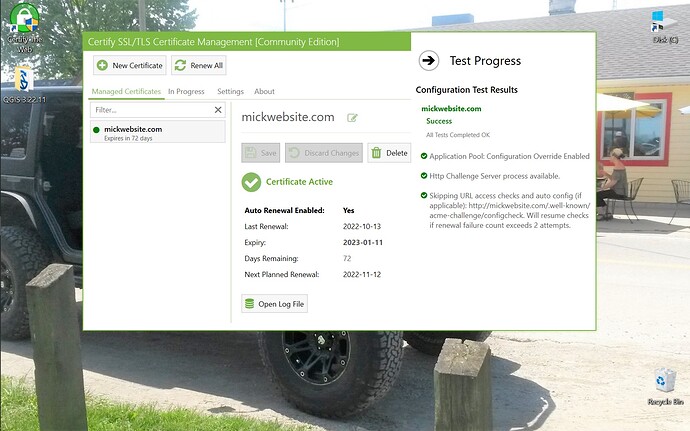
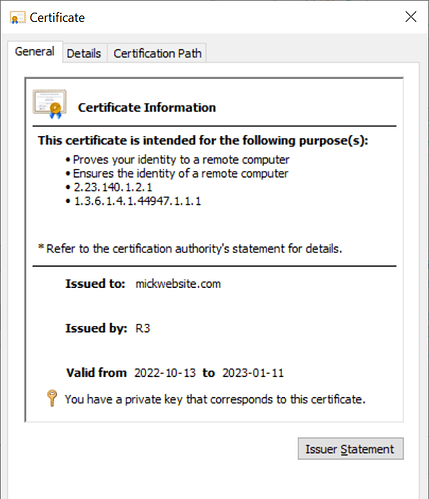
In the CTW app the certificate expires on 2023-01-11. When I run inetmgr in Windows 10 IIS I get a different certificate with expiry date, 22-11-02. I guess these are two different certificates? possibly acquired at different times? What should I do with this?
I haven’t really checked but the date in the UI is likely local time and the date on the actual certificate is likely UTC, so they’re just the same date interpreted differently. There is nothing you need to do and there is only one active certificate.
My best guess is that the dates would mean January 11th, 2023 and November 2nd, 2022. That’s not a timezone issue.
It might be easier to understand if screenshots were provided from IIS manager. There are places that display (too many) things and other places where you can choose different certificates. Also, knowing your region settings for how dates are displayed for your OS would be nice.
Interesting! The cert currently selected in IIS is not the one most recently renewed. Please grab a screenshot of the Preview tab in certify- the Deployment section should have a list of IIS bindings that will be updated and it would be interesting to see what that says.
Here is a copy of the text, easier than the screenshot ![]() Hope this has the info that you are looking for…
Hope this has the info that you are looking for…
Summary
A new certificate will be requested from the Default certificate authority for the following domains:
mickwebsite.com (Primary Domain)
1. Domain Validation
Authorization will be attempted using the http-01 challenge type.
The following matching domains will use this challenge:
-
mickwebsite.com
Please review the Deployment section below to ensure this certificate will be applied to the expected website bindings (if any).
This will involve the creation of a randomly named (extensionless) text file for each domain (website) included in the certificate.
The Http Challenge Server option is enabled. This will create a temporary web service on port 80 during validation. This process co-exists with your main web server and listens for http challenge requests to /.well-known/acme-challenge/. If you are using a web server on port 80 other than IIS (or other http.sys enabled server), that will be used instead.
The text file will need to be accessible from the URL http://<yourdomain>/.well-known/acme-challenge/<randomfilename>
The issuing Certificate Authority will follow any redirection in place (such as rewriting the URL to https) but the initial request will be made via http on port 80.
This challenge type will be selected for all domains.
2. Certificate Request
A Certificate Signing Request (CSR) will be submitted to the Certificate Authority, using the RS256 signing algorithm.
3. Deployment
- Deploy to hostname bindings matching certificate domains.
- Deploy to bindings with previous certificate.
- Add or Update https bindings as required
Deploying to all matching sites:
Certificate will be stored in the computer certificate store [My]
| Action | Site | Binding |
|---|---|---|
| Update https binding | Website | *:443:mickwebsite.com SNI |
Ok, that certainly looks correct. I can’t see any reason why the new cert has not updated in the IIS binding. In Certify try Certificate > Advanced > Actions > Re-apply Certificate to Bindings (option is at the bottom). If that’s working ok then the latest cert should be applied in IIS, so you can check that in IIS manager to confirm that the newer cert has been selected. If it’s still not updating, check that you can see the newer cert in the IIS binding dropdown list.
Great, odd that it didn’t apply the first time round but it should be ok now.
I did have TLS 1.0 and TLS 1.1 disabled for a while [a week or two?] in the registry. I had some information, apparently unreliable, that they were unnecessary. This is the only recent change in my Windows 10 setup. This also caused some problems with my website. Everything seems OK now.
I do not understand many of the complex of things here. I just work away at it, get help from good people like yourself, eventually things work out.
Thank you again ![]()
Mick