Hi @webprofusion,
This is more FYI rather than anything to think about immediately.
When using OpenSSL v3 (certain in Windows, but I guess also other OS) to analyse and covert a pks file generated through Certify the Web, you see an error due to the way it is packaged. Apparently, OpenSSL v3 doesn’t like older security algorithms. For example, if trying to extract the certificates from a “normal” pfx file, you may see the following error using OpenSSL 3.x:
PS C:\OpenSSL-Win64\bin\openssl.exe pkcs12 -in "my_old.pfx" -nodes
....
Error outputting keys and certificates
74800000:error:0308010C:digital envelope routines:inner_evp_generic_fetch:unsupported:crypto\evp\evp_fetch.c:349:Global default library context, Algorithm (RC2-40-CBC : 0), Properties ()
Running info against this pfx give us some more, er, info ![]()
C:\OpenSSL-Win64\bin\openssl.exe pkcs12 -in "my_old.pfx" -info -nokeys -nocerts
Enter Import Password:
MAC: sha1, Iteration 1024
MAC length: 20, salt length: 20
PKCS7 Data
Shrouded Keybag: pbeWithSHA1And3-KeyTripleDES-CBC, Iteration 1024
PKCS7 Encrypted data: pbeWithSHA1And40BitRC2-CBC, Iteration 1024
Error outputting keys and certificates
8C9D0000:error:0308010C:digital envelope routines:inner_evp_generic_fetch:unsupported:crypto\evp\evp_fetch.c:349:Global default library context, Algorithm (RC2-40-CBC : 0), Properties ()
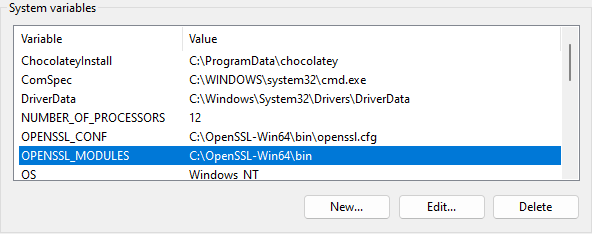
It appears as if you need to tell OpenSSL to use the legacy provider, however (and certainly in Windows) by default it doesn’t know where to get this provider dll. You, therefore, need to tell it where this is using the provider-path parameter, something like this:
PS C:\OpenSSL-Win64\bin\openssl.exe pkcs12 -in "my_old.pfx" -nodes -legacy -provider-path "C:\OpenSSL-Win64\bin"
However, you can be super cool and make things a bit simpler by adding an environment variable called OPENSSL_MODULES and pointing it to C:\OpenSSL-Win64\bin into the installer, so all you need to specify is the legacy option, which is at least not as much to remember and to type ![]()