Due to a power surge, my old server, which kept my 8 websites online flawlessly for over a decade, had to be replaced.
It is apparent that I have either forgotten everything I learned back then, or the process has gotten very complicated since.
I’m trying to get certificates for my 8 websites. I downloaded the Certify the Web app. I’m using Credential Type Namecheap DNS. I assume credential name is the root domain name of the site, so I put that in. But I don’t have anything to enter in API User and API Key fields. I put in my current IP address in the last field.
I tried looking this up on the web, but all I get back is complicated stuff about scripting APIs. I just want to know how to get these two fields filled in so I can get my certs and be one step closer to getting my life back after this power surge.
Hi, I totally know how hard it is to try to recover a service when it’s unexpectedly destroyed, I’d really recommend using cloud VM hosting (ideally with associated cloud backup) rather than running your own physical hardware. It depends, but I gave up on physical server hardware a long time ago and haven’t missed it.
If you were previously using the Namecheap DNS API then almost nothing has changed. The DNS API setup is really specific and you definitely cannot just guess the inputs. As an aside we’re actually going to deprecate our namecheap provider in favour of the one provided by the Posh-ACME project, however this one will still work as much as it currently does
See Namecheap - Posh-ACME and from that you get the following guidance:
First, login to your account and go to the Profile - Tools page. In the “Business & Dev Tools” section, API Access must be turned on. Namecheap seems to require a certain amount of activity (registered domains or money spent) in order to enable API Access. Turning it on requires Namecheap support to authorize and actually enable which can take a couple days.
Once API Access is turned on, click the Manage button and record your
API Keyvalue and your Namecheap username. You will also need to whitelist the public IP address of each machine you will be running Posh-ACME from. whatsmyip.com can help here if you’re behind a NAT router.
You can update the credentials in Certify The Web by looking under Settings > Stored Credentials and clicking the one you’ve added and hitting ‘Replace’. You will enter your Namecheap username and the API Key. Namecheap is a bit special and also ask you to provide your IP address (this is the external IP of your server as it would appear to them).
The title for the credential is just for you to know what it is when you see it, so Namecheap would be an example title if you only have one account, if you had multiple accounts then you’d probably name it after each account etc). For most users they would have multiple domains under one namecheap account, so naming it after one of the domains wouldn’t usually make much sense.
Once you have your credential entered and stored you can select it in your managed certificate under Authorization > (dns-01), NameCheap DNS API etc.
Then you can hit “Test” to try creating and removing an example TXT record in your DNS, if that all works then just hit “Request Certificate” to complete the normal certificate request.
This was somewhat helpful. I was in fact able to go into API Access at Namecheap and enable it, get the key and add it to the Certify the Web program.
I was able to generate and install a certificate under the IIS bindings for one website.
However, when I access the website, it’s still “not secure”. Note sure why, or what to do now.
I gave up on hosting services in 2005. Outages, recurring bills, lack of income, and never looked back. I just want to get back to having a reliable server like I did before the power surge fried my server. I got 15 good years out of it with zero downtime.
Always glad to be somewhat helpful. 15 years is a good stretch, I hope you’ve taken the opportunity to use the latest version of windows so you can get another 15 years out of it.
Regarding the ‘not secure’ issue, I can’t help without knowing the domain and having a look. I assume you are accessing the website via https. I also assume that you let Certify The Web create your https binding for you (if you created it yourself ensure it’s got SNI checked and you have set the hostname). If you don’t use SNI you can only have one certificate per server IP address, so you generally don’t want to do that. You will need to add your own URL rewrite rule if you want to automatically redirect http to https.
In general I recommend:
- setup your website with an http binding in IIS (port 80) and set the hostname (domain) in the binding for each variant (e.g.
www.domain.comanddomain.com) - do not leave the hostname blank, it’s necessary to match the certificate automatically to the correct website. - Add a new managed certificate in Certify The Web: select your IIS website and the domains (www.domain.com and domain.com etc) will be read from the existing IIS http bindings and automatically shown and selected ready for inclusion on your certificate. Set your preferred authorization method (http is usually fine, but DNS if you want to). Click the Preview tab to review that the expected bindings will be added/updated in IIS (see the bottom of the page).
- Click “Request Certificate” to automatically order your certificate from Let’s Encrypt, validate your domains and auto apply them to IIS bindings for the respective websites. Done.
After researching the issue, I found out that IIS does not have URL rewrite. So I had to fight again with the installer (which fails) and manually download and install URL Rewrite. Then I had to look up how to write the rule to upgrade HTTP to HTTPS. I did that. Now it’s using HTTPS, but instead of the site displaying, I am getting:
“You do not have permission to view this directory or page.”
Without URL rewrite, I get the unsecure page and it looks like the normal website. For some reason, when putting HTTPS in front of the URL, I get that permission error.
Windows 10 IIS has just been one long string of fights. Nothing works on the latest version! Backup Image fails, I can’t open log files (Admin doesn’t have permission to view), many features of IIS seem to be broken (can’t install new modules–fails every time). I’ve never seen so many problems in a new OS installation. Basic functions seem to be blocked or off limits. I’m seriously tempted to wipe the drive and install Windows 7 and get things working again. Windows 10 is garbage. Too locked down.
For a server I’d recommend actually using Windows Server (2022). Windows 10 is only barely suitable for hosting a website. You can turn of UAC prompts (to allow admin things) but I’ve never heard of not being able to open log files. If you are using committed to using a home or pro version of Windows use Windows 11 if you can, there’s no point using Windows 10 unless your hardware is incompatible. There’s no point going back to Windows 7 other than familiarity (Win 7 is nearly 12 years old).
For the ‘you do not have permission’ error, I assume you are doing this at home, and your internet comes in via an ISP router, so you have to forward the correct ports (TCP 80 and and TCP 443) to the correct machine - perhaps it’s IP address has changed.
Your website also needs default page (like index.html or default.aspx) and sometime you need to configure that default otherwise it will try to revert to directory browsing (which is normally disabled). It sounds like the http version works though, so that’s probably not the problem.
Are you using windows specific features for your websites (like old .net or .asp ?) otherwise a linux server on AWS (LightSail) costs $3.50 per month - it wouldn’t be easier but long term it’s pretty good. If your content is static (just html/images etc) you can use something like Netlify or Cloudflare pages and skip the server admin.
Btw I took the liberty of guessing your domain and basspig.com is currently serving the wrong https certificate, this is because one of your other https bindings in IIS is not using SNI (probably ampexperts.com) - you need to make sure that’s using SNI and a hostname is set in the IIS https binding. You also don’t generally want to have a ‘Default SSL website’ configured because it will take priority over other SSL bindings on the same IP address.
At the moment basspig.com isn’t bound to any certificate. I installed a certificate on ampexperts.com as that’s my income earning site, first.
Definately teh router and ISP connection are working, as those pages can be served http only.
I’m noticing that when I access my site with an android tablet, the tablet is prompting me to choose a certificate (as if the web site is asking the user to present a certificate that such user has the credentials to access the website!)
I looked into Windows Server a couple of years ago when I was struggling with the issue of only having SSL cert on one of my eight sites, but the cost of the subscription was something only corporations could afford.
I had heard there is a way to get one cert to cover all the websites, forgot what it was called… I knew this maybe 5-6 years ago… I did try making a cert that contained all 8 sites. Maybe that is causing the problem?
I’m on pretty much a zero budget. Can barely afford to keep paying for domain names as it is! I just want to get back to where I was 4 days ago, with 8 working websites.
Sure thing. I’ve thankfully graduated from the zero budget days but I remember it well.
The issue with being prompted for a client certificate is probably that client certificates has been switched on somewhere (i.e. the visitor for your website is expected to present their own certificate to authenticate themselves. Not usually what you want).
Ensure your SSL Settings option in IIS looks like this (for all sites):
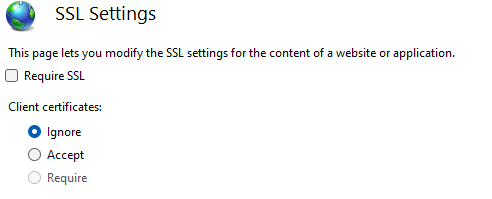
Regarding having one cert to cover all sites, you can do it - you would manually add the domains to one managed certificate then just let the app automatically add/update https bindings based on the IIS bindings you already have matching the hostname form the certificates. This would work by default if all of your websites are already setup with http (hostname) bindings and responding on http. However, it doesn’t have much advantage and if one website goes down then the whole certificate would fail to renew due the one website not responding or resolving etc.
The (free) community edition of Certify The Web will start to nag you about registration after the first couple of managed certificates but it currently allows 10 managed certificates on the free version, you just have to ignore the nag screen. Each managed certificate can cover up to 100 domains.
The SSL Settings you snapshotted above was it! I did not realize that was affecting this if the checkbox was unchecked! I set to ignore and now the site is up.
I think I’ll stick with individual certs. Does that nag screen stop or interfere with automatic renewals? Sometimes the server runs unattended for up to a year or more, especially if I’m overseas. I can’t have it stop updating because of a need to click through a nag screen.
Well this solves one major problem out of dozens of smaller ones. I still need to get PHP working, find out why Web Platform Installer fails, and find out why Windows Image Backup always fails with a “not enough space” error on even an 8TB backup drive. That last one’s a priority because if I can’t image the drive and something goes wrong, I’ve lost four days of work setting this all up.
I’ve made some progress, in that I can generate certificates now through the NameCheap DNS thanks to enabling that feature at NameCheap that you mentioned.
However, I’m running into a new problem: when I add a certificate to another site, the last site I made secure becomes unsecure and browsing to it I get a warning that attackers may be trying to steal my information. When I look into it further, I see something about ampexperts.com is using basspig.com certificate. But I had made sure that ampexperts bindings were to the ampexperts certificate. Also when I added the next certificate, I got a warning that “at least one other site is using the same HTTPS binding” and that something would be overwritten.
One of the reasons I upgraded to Win 10 was so that I could take advantage of the ability to have more than one secure site. I seem to be doing something wrong here.
- The nag about license will not interfere with renewals. All the managed certificates you have added will renew automatically as long as it knows which bindings to update. You can see which bindings it will update at the bottom of the Preview tab page.
- For your bindings, you’re doing something odd possibly because you think it’s required. Don’t setup https bindings yourself, let the app do it for you. Remove any https bindings you have manually created (all sites), ensure each site has a normal http (port 80) binding with the hostname set and then use the app to Request Certificate for each site.
In all cases you can review the Preview tab to see which bindings will be updated (bindings are different to the domains on your certificate, you could have 2 domains on your certificate but the app can’t find any bindings to update due to no hostname set, therefore no https bindings will be added).
Here is an example preview for binding updates:
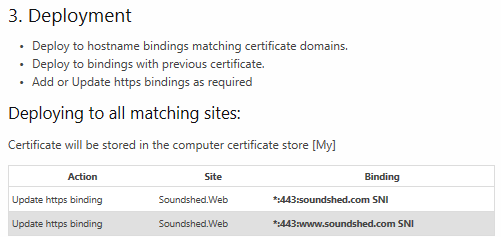
It’s ultra important that all https bindings in IIS use SNI (with hostname set) and do not have a specific IP address binding (use All Unassigned), otherwise that binding will steal the https certificate settings for all other sites sharing that IP. There are ways to work without SNI and use IP specific bindings, but only if you really understand that stuff and know why you’re doing it.
Apparently, I needed to check the box “require server name identification” to allow more than one cert.
However, I do get a warning that I need to configure a default SSL server for browsers that don’t support SNI. I don’t know how to do that.
Finally, if I enter the full qualified name with “www” in front, it loads. If I just type basspig (dot) com, the error “you don’t have permission to view this directory or page” occurs. How do I fix that?
Yes, Server Name Indication is the SNI I was referring to - try not to setup the https bindings yourself if you can avoid it and let the app do it for you instead. That way you can be sure that renewals will also update the correct bindings.
Ignore the IIS warning about creating a default SSL - that’s legacy stuff and it’s mostly irrelevant nowadays, enabling it will likely result in binding SSL conflicts. It dates back to the days before SNI where you basically needed your server to have multiple IP addresses in order to have multiple certificates.
You need a hostname binding in IIS (and a domain on your certificate) for every combination of website name. www.basspig.com is one hostname (a.k.a “subdomain” or subject alternative name), basspig.com is another and they both need to have bindings in IIS. You also need both of these names on your certificate.
Thank you. Adding “basspig(dot)com” for both http and https fixed the problem. Fortunately, I was mindful to create both URLs for each certificate.
Cool, after a couple of months check to ensure the certificates are renewing ok and the https bindings are being updated with the latest cert, after that it’s all good.
Yup, that’s always the thing… long term reliability. My old server had been tweaked to the point where it was totally fault tolerant (excepting power surge), so I didn’t have to touch it for several years and it just ran and ran.
Hopefully this new one will be as reliable. I’ll keep an eye on the certs.
Does this program need to be running, or is there a service installed that does the renewal in the background? Need to know if I should put the interface in the startup boot menu or not…
CTW has a service that always runs in the background. You only need to run the UI to configure things and to check up on how things are. There’s no requirement to run the UI on a regular basis. But it’s a good way to find out about program updates, etc.