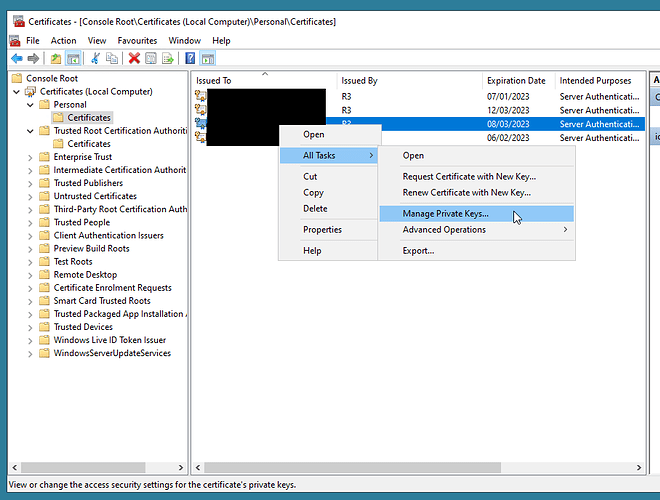
I used procmon to capture and confirm the problem when I tried to remote desktop in:
Time of Day Process Name PID Operation Path Result Detail
31:43.3 lsass.exe 1400 CreateFile C:\ProgramData\Microsoft\Crypto\RSA\MachineKeys\6f021f9dfe8e073c19841e9f6e5be9ba_ed053d70-8e6a-4081-8aa8-31b1245f1c3b ACCESS DENIED Desired Access: Generic Read, Disposition: Open, Options: Sequential Access, Synchronous IO Non-Alert, Non-Directory File, Attributes: n/a, ShareMode: Read, AllocationSize: n/a, Impersonating: NT AUTHORITY\NETWORK SERVICE
There is a way to edit the permissions using icacls but I found it much easier to do it using the MMC certificate plugin (as detailed in the article you linked to).
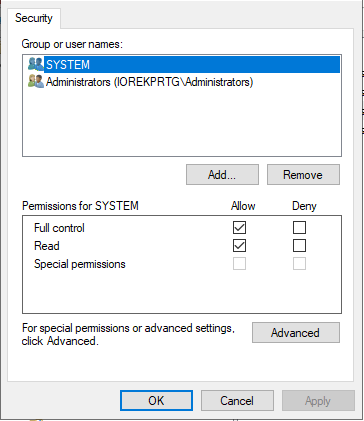
If I looked at a non-working certificate the only permissions were for system (full) and administrators (read).
(I’m a new user on this forum so it won’t let me post more than one picture)
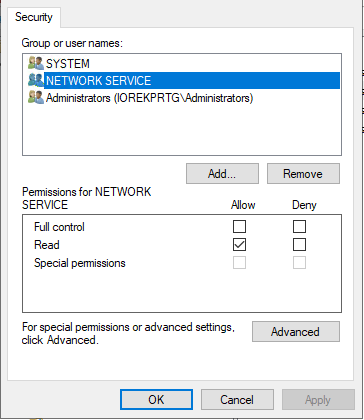
To ‘fix’ the problem I just had to add read access to NETWORK SERVICE
(I’m a new user on this forum so it won’t let me post more than one picture)
As I said, the only thing I had changed was moving from my script to ‘Deploy to RDP Listener Service’ instead. But my script doesn’t do anything with permissions, it just writes the thumbprint to the appropriate registry key!
# this grabs the certificate thumbprint and tells RDP to use it
$HOSTNAME="mycomputer.mydomain.com"
$THUMBPRINT = (ls Cert:\LocalMachine\my | WHERE {$_.Subject -match $HOSTNAME } | Sort-Object -Property NotAfter -Descending | Select-Object -First 1).Thumbprint
if (!$THUMBPRINT) {
write-host "Failed to find certificate thumbprint for ${HOSTNAME}, quitting."
} else {
write-host "Found certificate thumbprint for ${HOSTNAME}: ${THUMBPRINT}"
write-host "Configuring RDP"
& wmic /namespace:\\root\CIMV2\TerminalServices PATH Win32_TSGeneralSetting Set SSLCertificateSHA1Hash="$THUMBPRINT"
write-host `Done!`
}
Clearly I can’t explain why running my script as a powershell task adds a permission that your ‘Deploy to RDP Listener Service’ doesn’t. I double checked that it was running my script as a task that made the change by getting a new certificate and checking its permissions before and after my script ran.
I’m using the current release version, 5.6.8.0. I haven’t ever used the background service as a different user other than the default (Local System). I don’t have any other deployment tasks enabled.
Edit: BTW, I realise I could have passed the Thumbprint from Certify The Web as a variable but I haven’t tried using Certify The Web variables and I already had the script to reuse.