Is it possible through certifytheweb to renew the certificate for FTP SSL. Have to do it manually each time after certificate renewal for my domains. I am looking for a similar function like ”deploy to remote access services”. Otherwise a powershellscript to run after certificate deployment. Anyone know about such a script ?
Hi, we added (IIS) FTP binding support in v5, are you looking for something different? If it’s for IIS you should be able to see your ftp site in the list of host names for your selected IIS site, unless your ftp site and website share the same hostname.
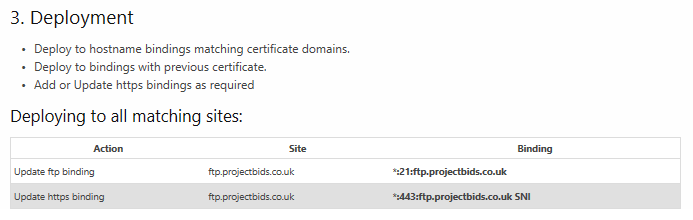
So for example, if I have a site ftp.projectbids.co.uk with both an ftp and http binding in IIS, the app will automatically maintain the following bindings (see the bottom of the Preview tab):
It does not seems to show like that on my end as well
how do I get that deploy table with the ftp binding?
using 5.6.8.0 for now
The deployment preview is shown in the Preview tab of your managed certificate (scroll down for deployment info). If no binding deployments are shown then nothing will be updated. Generally this means your existing binding do not have an appropriate hostname set, so the auto deployment can’t match the certificate against that site.
It appears under the Preview Tab once you set SNI (Hostname for FTP site in IIS). However, it defaults to port 21 rather than the port number set in the bindings for the FTP site. We use a custom port number to avoid simple FTP scanners. Current version I’m testing is v.6.0.12.0. Can it pickup the port number from the bindings?
Hi @dclarkenz our ftp support isn’t quite as comprehensive as our https support but there is currently a way you could get it to work I think.
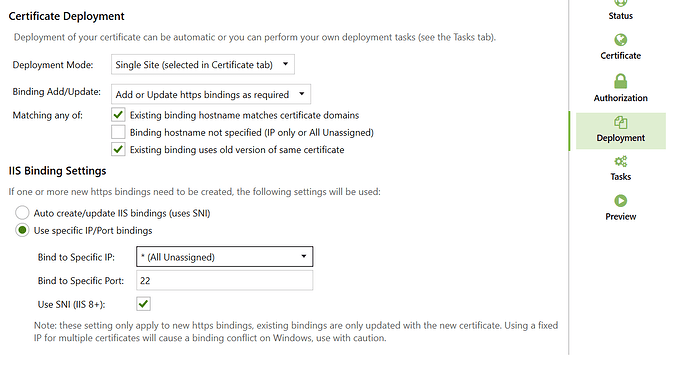
Https bindings will always re-use the existing port for the cert binding that’s already there, but ftp sites currently default to port 21 only.
If however you set Deployment Mode to Single Site and bind to specific port 22, the app will use port 22 for the ftp binding. This is a quirk of the current implementation rather than by design.
An alternative is to use a Powershell deployment task to update the FTP binding yourself, that has the benefit of giving you more discreet control over that specific binding.
[Our next update will include a fix for re-using the current ftp port binding just like it does for https, at that point you could set deployment mode back to auto if you wanted to]